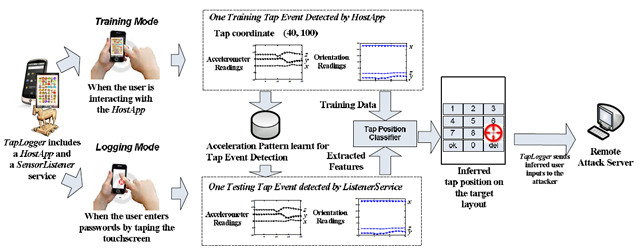
There is a trojan called TapLogger that logs and steals phone numbers, social security ID’s, and personal identification numbers by monitoring keystrokes based on tap location. By monitoring the device based on the integrated motion sensors TapLogger can track just about anything you do on your device. This trojan was created by computer scientists as a proof-of-concept app for phones running Android and hides itself as a game that challenges users to identify identical icons from similar looking images.
The trojan runs in the background and monitors readings returned by the phones accelerometer, gyro, and orientation sensors to collect anything entered into the device via a touch action. The information is then logged and uploaded to a remote machine under the attackers control for their own malicious uses.
“The fundamental problem here is that sensing is unmanaged on existing smartphone platforms,” Zhi Xu, a PhD candidate in the Pennsylvania State University’s Department of Computer Science and Engineering, wrote in an email to Ars. “TapLogger shows that those unmanaged ‘insensitive sensors’ can really be used to infer very sensitive user information (e.g. passwords and PIN numbers). Inspired by TapLogger, we believe that more and more sensor-based attackers will be introduced in the near future.”
TapLogger based on keystrokes on the device can figure out the taps of a given Android model and make very good guesses as to the buttons pushed. While the trojan cannot tell the attacker the exact sequence pressed it allows them to figure it out very easily.
“To prevent such types of attacks, we see an urgent need for sensing management systems on the existing commodity smartphone platforms,” they wrote. “Sensors, such as accelerometer and orientation sensors, should all be considered as sensitive to user’s privacy and need gaining security permissions to access.”
This is currently an Android built trojan although can easily infect iOS devices that have been jailbroken. Stock iOS devices are currently immune to the malicious threats although with these types of attacks growing rapidly we will likely see improved versions over time.